In this write-up, I'll show you the steps I took to solve HackThis "Main Level" challenges. Hope this helps if you get stuck at any level, or want to see maybe another approach.
As a general introduction, HackThis provides challenges for Information Security enthusiasts, hackers, etc. In all "Main Level" challenges, we will only see an HTML form, which asks for Username and Password. Our mission on each level is to fill out this form with correct credentials, by hacking into the system and gathering valid credentials.
Let's walkthrough all the "Main Level" challenges together:
Main Level 1
In this challenge, (and in all the upcoming challenges,) I started by viewing the source code of the webpage. In Google Chrome, you can simply right-click on the page, and choose View page source, or press CTRL + U. If you are using another web browser, you can try something similar, or simply Google "how to view page source in X", where X stands for your web browser (e.g. "how to view page source in Mozilla Firefox").
In the page source, I searched for the keyword Username, by pressing CTRL + F and typing the keyword. Upon searching, the browser displays 3 matches. Among these 3 matches, one of them brings the most attention:
<!-- username: in, password: out -->
This is an HTML comment, which cannot be seen on the webpage; but can easily be seen by looking at the source code. In the comment, we see that the developer left the credentials in the source code, as an HTML comment. So, when we try logging in with the username in, and password out; we are done!
Lessons Learned: If you are a web developer, never leave sensitive information as a comment. If you are a hacker, read through the comments in the source code, which can hold precious information. In terms of this challenge, obviously no developer would leave a credential in the comments; but other non-trivial information, or clues to understand the source code better can be left as comments.
Main Level 2
Again, I started by viewing the source code of the webpage, and searching for the keyword Username. This time, we encounter something very unusual:
We see that there is a span next to the Username field, having a color #000000 (which stands for black, in terms of RGB), which has a text: resu. Similarly, a span next to the Password field, with text ssap. So, we have found the username and the password already!
Moreover, since these texts are within the source code (uncommented), we should be able to see them on the webpage. The reason why we don't see them is since both the background color and the text color are black! By left-clicking and holding the mouse from the beginning of the webpage to the down, we see a highlighted version of the webpage, which holds the username and the password, as expected:
So yes, we are done!
Lessons Learned: It is impossible to hide information by just visual arrangements. There is the source code which shows everything within the webpage, and there are workarounds to some of the visual tricks.
Main Level 3
Again, let's look at the source code. This time, when I searched for the keyword "Username", I only got 2 matches, which didn't help too much. So, I decided to do another search related to the HTML form.
Each HTML form has to be submitted to the web server, so that the data entered reaches to the website. This is done with a submit action. Hence, I decided to search for the keyword submit. This search returned 6 matches, one of which was really interesting:
<script type='text/javascript'>
$(function(){
$('.level-form').submit(function(e){
if(document.getElementById('user').value == 'heaven' && document.getElementById('pass').value == 'hell') { }
else { e.preventDefault(); alert('Incorrect login') }
})
})
$('.level-form').submit(function(e){
if(document.getElementById('user').value == 'heaven' && document.getElementById('pass').value == 'hell') { }
else { e.preventDefault(); alert('Incorrect login') }
})
})
</script>
This code is a JavaScript function, which submits the .level-form. In particular, document.getElementById() function returns the HTML element with the corresponding ID. In this code, it is used twice; one for ID user and one for ID pass, which are actually the fields of our HTML form. We can see that the values heaven and hell are passed to the fields user and pass, respectively, in our HTML form; and an "Incorrect login" alert is issued if any other value is passed.
Hence, we try heaven as username, and hell as password. And, voilà! We are done!
Lessons Learned: JavaScript is an integral part of the websites today. Many JavaScript functions are being used in most of the websites; so one needs to pay attention to those functions, as they can hold precious information.
Main Level 4
Again, and again, I started by viewing the source code of the webpage. This time, searching for the keyword Username, and looking at the HTML form's source code gives an interesting result:
<form method="POST">
<fieldset>
<label for="user">Username:</label>
<input type="Text" name="user" id="user" autocomplete="off"><br>
<label for="user">Password:</label>
<input type="Password" name="pass" id="pass" autocomplete="off"><br>
<input type="hidden" name="passwordfile" value="../../extras/ssap.xml">
<input type="submit" value="Submit" class="button">
</fieldset>
</form>
<fieldset>
<label for="user">Username:</label>
<input type="Text" name="user" id="user" autocomplete="off"><br>
<label for="user">Password:</label>
<input type="Password" name="pass" id="pass" autocomplete="off"><br>
<input type="hidden" name="passwordfile" value="../../extras/ssap.xml">
<input type="submit" value="Submit" class="button">
</fieldset>
</form>
The highlighted code is present now, different from the older levels. It is a hidden HTML input field, which is hidden from the users. But as seen, we are able to look at the source code and see what is inside in the "hidden" field. We see that the hidden input field is named as passwordfile, which is an obvious hint to us, and its value is ../../extras/ssap.xml, which looks like a path to the passwordfile.
Now, I tried reaching to the file by entering this URL into the browser:
https://www.hackthis.co.uk/levels/main/4/../../extras/ssap.xml
As I expected, I encountered an XML file named ssap.xml:
<user>
<name>Admin</name>
<username>999</username>
<password>911</password>
</user>
This obviously shows that there is an Admin user, having username 999 and password 911. Upon entering this information, we are done!
Lessons Learned: Hidden HTML fields are not hidden! Moreover, files inside a website could be reached by traversing through directories. For securing the website, the access to each file should be controlled; only authorized users should be able to reach them.
Main Level 5
Now, a dialogue box welcomes us upon entering the website, asking for a Password. So, I again looked at the source code of the website; but this time searching for the keyword "Password", as it appeared in the dialogue box. The first occurrence seems quite interesting:
<script language="JavaScript" type="text/javascript">
var pass;
pass=prompt("Password","");
if (pass=="9286jas") {
window.location.href="/levels/main/5?pass=9286jas";
}
</script>
var pass;
pass=prompt("Password","");
if (pass=="9286jas") {
window.location.href="/levels/main/5?pass=9286jas";
}
</script>
As seen above, we again have a JavaScript code, as in Main Level 3. This script prompts for a Password, which is the password we are asked on the screen we encounter once we visit the website. We notice the if-statement inside the above script:
if (pass=="9286jas") {
This means that if the string 9286jas is entered when the prompt dialogue box appears, the website will be redirected to the href: /levels/main/5?pass=9286jas. If we enter that password, we are redirected to that hyper reference, and we are done with the level! Moreover, noticing that we are done upon being directed to that website, we can simply enter that URL to our browser, and we are done without even entering an input to the prompt dialogue box!
Lessons Learned: Again as Main Level 3, pay close attention to JavaScript code!
Main Level 6
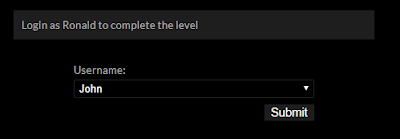
This time, a different login screen welcomes us; informing that we need to login as Ronald to pass the level. However, there is a small issue here. There is no option as Ronald in the Username list below!
So, we need to somehow modify the username, outside the website. We should notice a fact here.
Since we use a browser to browse the web, which satisfies our daily purposes, the machine-to-machine interaction goes between the website and our browser. They understand each other using a protocol, called HyperText Transfer Protocol, HTTP, or a secure version of the HTTP, which is HyperText Transfer Protocol over Secure Socket Layer, HTTPS.
For special modifications, we should either use a program, browser plugin, or maybe even write our own program. However, for the purposes of this level, to modify the Username, I used Google Chrome itself. If your browser supports modifications, you also can simply use your own browser to pass the level.
Hovering the mouse on the username list field, I right clicked the webpage, chose Inspect among the options. This option gives us the chance to inspect the specific elements of the webpage easily, without the need to search through the source code. Moreover, it has an ability to modify the code, which we are going to see in seconds.
Inspecting the element, we get the following result:
| <select id="user" name="user"> <option>John</option> <option>Petter</option> <option>David</option> <option>Sam</option> </select> |
This is the list of the usernames. To be able to login as Ronald, I double clicked one of the options on the Inspect pane of Google Chrome, say David, changed the text "David" to "Ronald". Then, I chose Ronald from the options on the website, clicked to Submit button, and it's done!
Lessons Learned: Don't trust to the users! The client-side code can always be changed! To provide the integrity of the data, and to protect against tampering, websites should implement server-side checks. The data sent from the user should always be controlled. No assumption should be made on the data coming from the user at the server side.
The next part of this write-up, i.e., Main Level 7-10 Solutions can be found via this link.




Many thanks. I solved Level 6 with Firefox.
ReplyDeleteYou're welcome, thank you for reading my post and providing extra context!
DeleteYou made such an interesting piece to read, giving every subject enlightenment for us to gain knowledge. Thanks for sharing the such information with us to read this... Serious Security Sydney
ReplyDeleteHello Hales! Thank you for your kindness, I am glad to be of help. Sorry for my late reply, I haven't been monitoring my blog lately.
DeleteThis professional hacker is absolutely reliable and I strongly recommend him for any type of hack you require. I know this because I have hired him severally for various hacks and he has never disappointed me nor any of my friends who have hired him too, he can help you with any of the following hacks:wifi hacking
ReplyDeleteYou made some decent points there. I looked on-line for your issue and found most people should go coupled with together with your internet site. white house market
ReplyDelete